David Baxter PhD
Late Founder
How Windows Defender’s Artificial Intelligence stopped malware
by AnkitGupta, TheWindowsClub.com
February 17, 2018
Ever imagined that a new malware attack stopped in its tracks by Artificial Intelligence? This possibility is brought to life by Microsoft with its antivirus, Windows Defender. According to a blog on Microsoft Secure, Windows Defender AV’s layered machine learning enabled the AV to stop the malware attack. Windows Defender AV not only uncovered the newly launched attack but also blocked it at the outset. That’s certainly a new and advanced way to stop the malware attacks.
Windows Defender’s Artificial Intelligence stopped malware
According to the blog, a Windows 7 Pro customer in North Carolina became the first would-be victim of a new malware attack campaign for Trojan:Win32/Emotet. Within the next 30 minutes, the malware campaign tried to attack over a thousand potential victims. However, all these Windows users were instantly and automatically protected by Windows Defender AV.
The blog mentions how Windows Defender AV was able to do this. The antivirus uses both client-side and cloud machine learning (ML) models. With the help of these two models, artificial intelligence enables Windows Defender AV to stop countless malware outbreaks in their tracks.
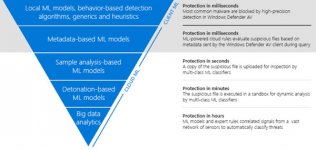
The blog further mentions in detail how these two models work to stop malware attack.
The blog further mentions,
The real-time cloud machine learning models work in following way:
For further details on Windows Defender AV’s Artificial Intelligence model, read the blog on Microsoft Secure blog.
by AnkitGupta, TheWindowsClub.com
February 17, 2018
Ever imagined that a new malware attack stopped in its tracks by Artificial Intelligence? This possibility is brought to life by Microsoft with its antivirus, Windows Defender. According to a blog on Microsoft Secure, Windows Defender AV’s layered machine learning enabled the AV to stop the malware attack. Windows Defender AV not only uncovered the newly launched attack but also blocked it at the outset. That’s certainly a new and advanced way to stop the malware attacks.
Windows Defender’s Artificial Intelligence stopped malware
According to the blog, a Windows 7 Pro customer in North Carolina became the first would-be victim of a new malware attack campaign for Trojan:Win32/Emotet. Within the next 30 minutes, the malware campaign tried to attack over a thousand potential victims. However, all these Windows users were instantly and automatically protected by Windows Defender AV.
The blog mentions how Windows Defender AV was able to do this. The antivirus uses both client-side and cloud machine learning (ML) models. With the help of these two models, artificial intelligence enables Windows Defender AV to stop countless malware outbreaks in their tracks.

The blog further mentions in detail how these two models work to stop malware attack.
“The first layer of machine learning protection is an array of lightweight ML models built right into the Windows Defender AV client that runs locally on your computer. Many of these models are specialized for file types commonly abused by malware authors, including, JavaScript, Visual Basic Script, and Office macro. Some models target behavior detection, while other models are aimed at detecting portable executable (PE) files (.exe and .dll).”
The blog further mentions,
“In the case of malware attack (mentioned above), Windows Defender AV caught the attack using one of the PE gradient boosted tree ensemble models. This model classifies files based on a featurization of the assembly opcode sequence as the file is emulated, allowing the model to look at the file’s behavior as it was simulated to run.”
The real-time cloud machine learning models work in following way:
“The cloud protection service is queried by Windows Defender AV clients billions of times every day to classify signals, resulting in millions of malware blocks per day, and translating to protection for hundreds of millions of customers.”
For further details on Windows Defender AV’s Artificial Intelligence model, read the blog on Microsoft Secure blog.
