David Baxter PhD
Late Founder
Protecting yourself from POODLE attacks
By Susan Bradley, Windows Secrets
October 22, 2014
No, this isn’t about Fluffy gone rogue. To keep our online browsing safe, we rely heavily security protocols — the “S” in HTTPS.
But a new exploit — POODLE — shows that commonly used security protocols aren’t as secure as we thought; websites and browsers will both need an upgrade.
Pulling a new trick on a very old dog
By now, it might seem that an exploit is serious only if it has a catchy name attached to it. (I won’t go down the list of clever names; doing so might get Windows Secrets blocked by overly cautious ISPs.) The latest threat is Padding Oracle On Downgraded Legacy Encryption — POODLE, for short. That’s not a name that immediately brings viciousness to mind. As a poodle owner over the years, my greatest worry was being licked to death. But the recently revealed weakness in the Secure Sockets Layer (SSL) protocol that allows the POODLE exploit has the digital-security world worrying about a new round of nasty malware bites.
Perhaps most problematic, there’s no quick patch or easy fix; the flaw is hard-coded within SSL 3.0. As Scott Helme explains on his blog, the “attack, specifically against the SSLv3 protocol, allows an attacker to obtain the plaintext of certain parts of an SSL connection, such as the cookie.”
A note on terminology here: SSL and TLS (Transport Layer Security) are often referred to simply as SSL. However, TLS officially replaced the SSL 3.0 protocol over a decade ago. But like most things on the Web, the SSL 3.0 protocol lives on and is still in widespread use. (See the Wikipedia article, Transport Layer Security for more details.) In short, the SSL protocols are all vulnerable; the TLS protocols, as far as we know, aren’t.
The POODLE exploit compromises the SSL protocol by forcing the server/browser connection to downgrade its TLS connection to SSL 3.0. That change allows leaks of cookie information, which could then lead to the disclosure of sensitive, personal information.
Fortunately, POODLE is not an easy exploit. It might take an attacker several hundred HTTPS requests before successfully forcing the Web server and a client browser to downgrade to a vulnerable SSL connection. On the other hand, the Web’s patchwork nature gives POODLE exploits an extremely large kennel to work in.
Protecting browsers from POODLE attacks
Most of us have two or more browsers installed on our systems. Unlike a Windows fix, there’s no one patch that will protect our browsers from POODLE. Instead, we must make adjustments within each browser; with Firefox, we must also download and use a Mozilla add-on until a new version of Firefox arrives in a month or so.
Be aware: After making these adjustments, you might find that business websites don’t work properly. So I recommend making the following adjustments to one browser and leaving another browser for those sites that are still waiting for the changes needed to protect themselves from POODLE. (Again, the fix for this exploit has to happen on both ends of Internet connections — the client and the server.)
The following changes force your browser to not use SSL 3.0. Here’s what to adjust in the top three browsers.
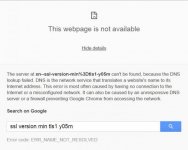
Chrome: In Google’s browser, edit the shortcut that launches the browser, adding a flag to the end of the Shortcut path. Start by selecting the icon normally used to launch Chrome. Right-click the icon and select Properties. Under the Shortcut tab, find the box labeled “Target” and insert -ssl-version-min=tls1 immediately after chrome.exe” (see Figure 1). It should look something like this (note the space between .exe” and –ssl-):
“C:\Program Files (x86)\Google\Chrome\Application\chrome.exe” -ssl-version-min=tls1
(Note: If your original Chrome path doesn’t start and end with quotes, don’t add one after chrome.exe.)
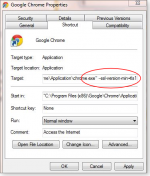
Figure 1. Disable SSL 3.0 support in Chrome by adding a flag at the end of the Properties/Target path.
From now on, launch Chrome only with this edited shortcut. Launching the browser from any unedited launch icons won’t provide protection from POODLE. Consider clicking on the General tab in the Chrome Properties dialog box and giving the edited shortcut a unique name — such as “Chrome – no SSLv3″ or something similar. Then you’ll always know you’re using the right shortcut.
Firefox: As noted in the Oct. 14 Mozilla blog, Firefox 34, due to be released on Nov. 25, will disable SSL 3.0 support. In the meantime, Mozilla recommends installing the SSL Version Control 0.2 add-on (see Figure 2) which will let you control SSL support within the browser. (Some websites have recommended adjusting Firefox settings in the configuration file, but Mozilla recommends using the add-on instead.)
Figure 2. To disable SSL 3.0 support in Firefox, Mozilla offers a browser add-on.
Internet Explorer: In IE, click the gear (settings) icon, open Internet options, and then select the Advanced tab. Scroll down the Settings list to the Security category, and then look for Use SSL 3.0. Uncheck the box (see Figure 3), click OK, and then relaunch IE.
Network admins can make this change to all PCs on the local network via Windows’ Group policy. Go to the Internet Explorer settings and modify the Turn off encryption support object (Windows Components\Internet Explorer\Internet Control Panel\Advanced Page).
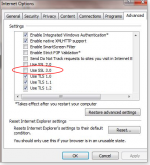
Figure 3. In IE, uncheck "Use SSL 3.0" in the advanced settings dialog box.
Microsoft released an initial security advisory on this topic; expect to see additional guidance in the near future.
How to test your browser’s TLS/SSL protection
Several websites test whether your currently open browser supports SSL 3.0. For a simple test, Poodletest.com displays a poodle dog if your browser still supports SSL 3.0, and a Springfield terrier if it doesn’t. On the other hand, Qualys SSL Labs provides a more detailed analysis of the SSL protocols your browser supports.
As noted above, some business sites such as online banking might still need SSL 3.0. Again, I recommend leaving SSL 3.0 support on one browser; it’ll be faster and safer than repeatedly adjusting browser settings. If you’re running a Web server or small-business server, you should disable SSL 3.0 support to better protect connected workstations and Internet-based phones.
An InfoSec Community Forums Incidents.org page lists how to block SSL 3.0 on various Web-based platforms.
For example, in Windows Server, create (or modify) a Registry DWORD value as follows:
Compromised cert highlights a system in doubt
POODLE is a clear indication that the TLS/SSL system we rely on needs work. In fact, the entire system of security protocols and certificates could well be a house of cards. For example, HP recently announced that one of its certificates has been used to sign malware. As noted in a Krebs on Security post, HP will revoke on Oct. 21 the certificate it has used for some of the software that shipped with older products. Unfortunately, HP isn’t completely sure what impact that change will have on the ability to restore some HP computers. Look for my future updates on that topic.
Another round in the dogfight over Internet security. As has been widely noted, POODLE effectively kills the SSL 3.0 protocol. Following the aforementioned steps, let’s make sure POODLE’s bark is worse than its bite (sorry, I couldn’t help myself). However, there’s a silver lining to this latest security mess — it should now force everyone on the Internet to finally abandon a dated, insecure protocol.
By Susan Bradley, Windows Secrets
October 22, 2014
No, this isn’t about Fluffy gone rogue. To keep our online browsing safe, we rely heavily security protocols — the “S” in HTTPS.
But a new exploit — POODLE — shows that commonly used security protocols aren’t as secure as we thought; websites and browsers will both need an upgrade.
Pulling a new trick on a very old dog
By now, it might seem that an exploit is serious only if it has a catchy name attached to it. (I won’t go down the list of clever names; doing so might get Windows Secrets blocked by overly cautious ISPs.) The latest threat is Padding Oracle On Downgraded Legacy Encryption — POODLE, for short. That’s not a name that immediately brings viciousness to mind. As a poodle owner over the years, my greatest worry was being licked to death. But the recently revealed weakness in the Secure Sockets Layer (SSL) protocol that allows the POODLE exploit has the digital-security world worrying about a new round of nasty malware bites.
Perhaps most problematic, there’s no quick patch or easy fix; the flaw is hard-coded within SSL 3.0. As Scott Helme explains on his blog, the “attack, specifically against the SSLv3 protocol, allows an attacker to obtain the plaintext of certain parts of an SSL connection, such as the cookie.”
A note on terminology here: SSL and TLS (Transport Layer Security) are often referred to simply as SSL. However, TLS officially replaced the SSL 3.0 protocol over a decade ago. But like most things on the Web, the SSL 3.0 protocol lives on and is still in widespread use. (See the Wikipedia article, Transport Layer Security for more details.) In short, the SSL protocols are all vulnerable; the TLS protocols, as far as we know, aren’t.
The POODLE exploit compromises the SSL protocol by forcing the server/browser connection to downgrade its TLS connection to SSL 3.0. That change allows leaks of cookie information, which could then lead to the disclosure of sensitive, personal information.
Fortunately, POODLE is not an easy exploit. It might take an attacker several hundred HTTPS requests before successfully forcing the Web server and a client browser to downgrade to a vulnerable SSL connection. On the other hand, the Web’s patchwork nature gives POODLE exploits an extremely large kennel to work in.
Protecting browsers from POODLE attacks
Most of us have two or more browsers installed on our systems. Unlike a Windows fix, there’s no one patch that will protect our browsers from POODLE. Instead, we must make adjustments within each browser; with Firefox, we must also download and use a Mozilla add-on until a new version of Firefox arrives in a month or so.
Be aware: After making these adjustments, you might find that business websites don’t work properly. So I recommend making the following adjustments to one browser and leaving another browser for those sites that are still waiting for the changes needed to protect themselves from POODLE. (Again, the fix for this exploit has to happen on both ends of Internet connections — the client and the server.)
The following changes force your browser to not use SSL 3.0. Here’s what to adjust in the top three browsers.
Chrome: In Google’s browser, edit the shortcut that launches the browser, adding a flag to the end of the Shortcut path. Start by selecting the icon normally used to launch Chrome. Right-click the icon and select Properties. Under the Shortcut tab, find the box labeled “Target” and insert -ssl-version-min=tls1 immediately after chrome.exe” (see Figure 1). It should look something like this (note the space between .exe” and –ssl-):
“C:\Program Files (x86)\Google\Chrome\Application\chrome.exe” -ssl-version-min=tls1
(Note: If your original Chrome path doesn’t start and end with quotes, don’t add one after chrome.exe.)

Figure 1. Disable SSL 3.0 support in Chrome by adding a flag at the end of the Properties/Target path.
From now on, launch Chrome only with this edited shortcut. Launching the browser from any unedited launch icons won’t provide protection from POODLE. Consider clicking on the General tab in the Chrome Properties dialog box and giving the edited shortcut a unique name — such as “Chrome – no SSLv3″ or something similar. Then you’ll always know you’re using the right shortcut.
Firefox: As noted in the Oct. 14 Mozilla blog, Firefox 34, due to be released on Nov. 25, will disable SSL 3.0 support. In the meantime, Mozilla recommends installing the SSL Version Control 0.2 add-on (see Figure 2) which will let you control SSL support within the browser. (Some websites have recommended adjusting Firefox settings in the configuration file, but Mozilla recommends using the add-on instead.)

Figure 2. To disable SSL 3.0 support in Firefox, Mozilla offers a browser add-on.
Internet Explorer: In IE, click the gear (settings) icon, open Internet options, and then select the Advanced tab. Scroll down the Settings list to the Security category, and then look for Use SSL 3.0. Uncheck the box (see Figure 3), click OK, and then relaunch IE.
Network admins can make this change to all PCs on the local network via Windows’ Group policy. Go to the Internet Explorer settings and modify the Turn off encryption support object (Windows Components\Internet Explorer\Internet Control Panel\Advanced Page).

Figure 3. In IE, uncheck "Use SSL 3.0" in the advanced settings dialog box.
Microsoft released an initial security advisory on this topic; expect to see additional guidance in the near future.
How to test your browser’s TLS/SSL protection
Several websites test whether your currently open browser supports SSL 3.0. For a simple test, Poodletest.com displays a poodle dog if your browser still supports SSL 3.0, and a Springfield terrier if it doesn’t. On the other hand, Qualys SSL Labs provides a more detailed analysis of the SSL protocols your browser supports.
As noted above, some business sites such as online banking might still need SSL 3.0. Again, I recommend leaving SSL 3.0 support on one browser; it’ll be faster and safer than repeatedly adjusting browser settings. If you’re running a Web server or small-business server, you should disable SSL 3.0 support to better protect connected workstations and Internet-based phones.
An InfoSec Community Forums Incidents.org page lists how to block SSL 3.0 on various Web-based platforms.
For example, in Windows Server, create (or modify) a Registry DWORD value as follows:
- In your Registry editor, go to: HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
- Under the Protocols, create a key called “SSL 3.0.” Then, under that key, create another key called “Server.”
- Create a DWORD called “Enabled” and give it a value of 0.
- Reboot the server; you and any connected clients will now be protected from POODLE exploits.
Compromised cert highlights a system in doubt
POODLE is a clear indication that the TLS/SSL system we rely on needs work. In fact, the entire system of security protocols and certificates could well be a house of cards. For example, HP recently announced that one of its certificates has been used to sign malware. As noted in a Krebs on Security post, HP will revoke on Oct. 21 the certificate it has used for some of the software that shipped with older products. Unfortunately, HP isn’t completely sure what impact that change will have on the ability to restore some HP computers. Look for my future updates on that topic.
Another round in the dogfight over Internet security. As has been widely noted, POODLE effectively kills the SSL 3.0 protocol. Following the aforementioned steps, let’s make sure POODLE’s bark is worse than its bite (sorry, I couldn’t help myself). However, there’s a silver lining to this latest security mess — it should now force everyone on the Internet to finally abandon a dated, insecure protocol.
Last edited: