David Baxter PhD
Late Founder
Windows Defender Offline ? old name, new use
By Woody Leonhard, Windows Secrets
January 5, 2012
Microsoft?s newly released beta version of Windows Defender Offline, a rootkit-sniffing and Windows-rehabilitation tool, should be the latest addition to your bag of Windows-repair tricks.
WDO should be able to catch a wide variety of nasties that evade detection by more traditional antivirus methods.
Although the name?s been around for years, don?t confuse this new version of WDO with previous incarnations ? it?s a whole new animal and helps PC users in two very different situations:
1. Windows won?t boot: You can boot your machine with a WDO CD or USB drive, and WDO will perform a detailed malware scan.
2. You suspect you have a rootkit: WDO can scan your system and remove many different kinds of rootkits.
Oddly, Microsoft has been uncharacteristically mum about Windows Defender Offline. If there are any published technical details about the program ? what it does or how it works ? I haven?t found them. With a bit of reading between the lines, here?s what I can say:
WDO is almost identical to an earlier product called Microsoft Standalone System Sweeper. Microsoft released the beta version of MSSS in May. (Susan Bradley?s July 28 Top Story talked about MSSS.) The size of the program hasn?t changed. The format of the signature files appears to be identical. The earlier product doesn?t mention Windows 8, but WDO most definitely does run on Win8 Developer Preview.
As best I can tell, WDO uses the same signature files used by Microsoft Security Essentials (MSE). However, I know of one instance where a piece of malware was not caught by MSE but did trigger a WDO response. I have no idea why.
I?ve seen no published statistics about WDO?s ability to identify or clean rootkits. But one possible reason WDO found malware that MSE could not find lies in the way WDO works.
Unlike MSE, WDO doesn?t depend on the Windows OS installed on your computer. It?s completely self-contained ? boot the afflicted PC from a WDO CD or USB drive, and the tool examines the system without any interference from the installed copy of Windows.
That?s critical for finding rootkits, which are very good at hiding on your system. Here?s an analogy: To make a watermelon smoothie, you?ve sliced the melon, removed the seeds, and mixed the cleaned pulp in a blender. Now imagine trying to pull a wayward seed (a missed rootkit) out of the blender while it?s running. That?s what rootkit extractors are up against: they need to find, isolate, and remove the rootkit while the Windows system is whirring away. Extracting malware is far easier when Windows is off.
Get a copy of Windows Defender Offline beta
As best I can tell ? Microsoft hasn?t published the details ? WDO will work on Windows XP SP3 systems (and possibly SP2); Vista RTM, SP1, and SP2; Windows 7 RTM and SP1; and Windows 8 Developer Preview. Also, your system must be bootable from a USB drive or a CD drive.
There are separate versions of WDO for 32-bit and 64-bit Windows, so you need to know the bittedness of the system to be scanned. (If you need help, see the Microsoft Help & How-to page, ?Is my PC running the 32-bit or 64-bit version of Windows??)
You can download WDO and create the bootable CD or USB drive on any handy computer, as long as it?s connected to the Internet. Here?s how:
1. Go to the Windows Defender Offline Beta site and, at the bottom of the page, click the link for either the 32-bit or 64-bit version. (Note, that the version needs to match the bittedness of the machine you?re fixing ? the bittedness of the machine you?re using to download WDO and create a bootable disc or drive doesn?t matter.)
2. Run the downloaded file to start the WDO installer ? you?ll see an initial splash screen with general WDO information. Click Next, and a new window appears that lets you choose where to install WDO, as shown in Figure 1. (Caution: Select the bootable USB drive option, and the installer wipes out everything currently on the USB drive.)
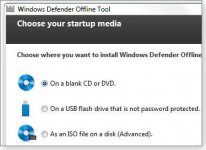
Figure 1. WDO must be installed on bootable media. The ISO-file option is used primarily to boot virtual machines.
3. Make your media selection and click Next. The installer downloads the latest version of the software and signature files (about 210MB for the 32-bit version or 230MB for the 64-bit version) and then creates the boot drive or the ISO file.
If you have problems creating a bootable drive, Microsoft?s WDO FAQ might have the answer.
Check your PC with Windows Defender Offline
It?s now time to boot your suspect system with the newly created WDO CD, DVD, or USB drive. If you need help with this step ? or your system won?t recognize the boot media (due, for example, to incorrect BIOS settings) ? the WDO FAQ page has some possible solutions (although the suggestion for disabling DEP is completely unnecessary).
If you have a multiboot system, you must choose which operating system to scan ? WDO will check only one at a time. With the OS selected, WDO next displays its command screen. (See Figure 2.)
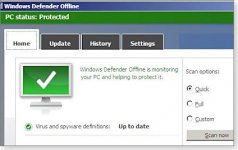
Figure 2. Windows Defender Offline?s command screen looks a lot like Microsoft Security Essentials.
If it?s been a while since you created the WDO boot drive and the PC being scanned is connected to the Internet, you?ll most likely want to click the Update tab and download the latest definition files.
Before clicking the Scan now button, select from the Quick, Full, or Custom scan options. A full scan is very thorough ? it looks inside all the files on the system, including ancient backed-up e-mails ? and can take up to eight hours to complete. (In tests on a relatively fresh Windows 8 Developer Preview virtual machine, a full scan took only 20 minutes.) The Custom option lets you select specific drives and folders to scan. A Quick scan looks in the most commonly used locations on your PC.
If WDO finds potential threats, it displays warnings identical to those in Microsoft Security Essentials ? and, like MSE, it lets you remove, quarantine, or ignore each threat.
Microsoft?s ongoing problem of brand confusion
Microsoft seems to be playing around with ? and botching ? its brands again. You may remember the Windows Live ID branding stupidity: the same product was originally called Microsoft Wallet, then MS Passport, then .NET Passport, then MS Passport Network before finally being christened Windows Live ID. Similarly, MSN Messenger became MSN Messenger Service, which ran on the .NET Messenger Service (or was it Windows Messenger?); then it all suddenly morphed into Windows Live Messenger. The term .NET has gone through so many marketing wringers, it?s hard to keep track: is .NET a floor wax or a dessert topping? Microsoft has a habit of bewildering you with product name changes and confusing product pedigrees for no apparent reason; the term Windows Defender is about to join the club.
The branding history of WDO goes something like this. Back in 2004, Microsoft bought a company called GIANT AntiSpyware and turned that product into Microsoft AntiSpyware the next year. MS then rewrote it and renamed it Windows Defender in 2006 ? and made it a free download for Windows XP. Later, MS built Windows Defender into Vista and Windows 7.
In 2005, Microsoft also bought a company called Sybari and turned Sybari?s antivirus product into a corporate AV suite ? Microsoft Forefront. Many companies are still running Forefront.
Microsoft then created a free, consumer/small-business version of Forefront and called it Microsoft Security Essentials. If you download and install MSE on a PC that has Windows Defender (whether manually installed on XP or baked into Vista and Win7), it automatically disables the Windows Defender user interface and takes over Defender?s functions ? MSE effectively supersedes Windows Defender.
It now appears that Microsoft is recycling the Windows Defender name, but none of the original WD code. Windows President Steve Sinofsky, who?s in the thick of finishing Windows 8, stated in a Building Windows 8 blog, ?With Windows 8, we are extending the protections provided by Defender to address a broader range of potential threats.? He added that Win8 will have ?improvements to Windows Defender to provide you with real-time protection from all categories of malware ?.?
In short, there?s every indication that Windows Defender Offline is based on the Forefront/Microsoft Security Essentials code base and has absolutely nothing in common with the old Windows Defender ? regardless of what you may have read in the computer press.
Regardless of its history, Windows Defender Offline?s primary advantage is as a self-booting anti-malware system. Try it out!
By Woody Leonhard, Windows Secrets
January 5, 2012
Microsoft?s newly released beta version of Windows Defender Offline, a rootkit-sniffing and Windows-rehabilitation tool, should be the latest addition to your bag of Windows-repair tricks.
WDO should be able to catch a wide variety of nasties that evade detection by more traditional antivirus methods.
Although the name?s been around for years, don?t confuse this new version of WDO with previous incarnations ? it?s a whole new animal and helps PC users in two very different situations:
1. Windows won?t boot: You can boot your machine with a WDO CD or USB drive, and WDO will perform a detailed malware scan.
2. You suspect you have a rootkit: WDO can scan your system and remove many different kinds of rootkits.
Oddly, Microsoft has been uncharacteristically mum about Windows Defender Offline. If there are any published technical details about the program ? what it does or how it works ? I haven?t found them. With a bit of reading between the lines, here?s what I can say:
WDO is almost identical to an earlier product called Microsoft Standalone System Sweeper. Microsoft released the beta version of MSSS in May. (Susan Bradley?s July 28 Top Story talked about MSSS.) The size of the program hasn?t changed. The format of the signature files appears to be identical. The earlier product doesn?t mention Windows 8, but WDO most definitely does run on Win8 Developer Preview.
As best I can tell, WDO uses the same signature files used by Microsoft Security Essentials (MSE). However, I know of one instance where a piece of malware was not caught by MSE but did trigger a WDO response. I have no idea why.
I?ve seen no published statistics about WDO?s ability to identify or clean rootkits. But one possible reason WDO found malware that MSE could not find lies in the way WDO works.
Unlike MSE, WDO doesn?t depend on the Windows OS installed on your computer. It?s completely self-contained ? boot the afflicted PC from a WDO CD or USB drive, and the tool examines the system without any interference from the installed copy of Windows.
That?s critical for finding rootkits, which are very good at hiding on your system. Here?s an analogy: To make a watermelon smoothie, you?ve sliced the melon, removed the seeds, and mixed the cleaned pulp in a blender. Now imagine trying to pull a wayward seed (a missed rootkit) out of the blender while it?s running. That?s what rootkit extractors are up against: they need to find, isolate, and remove the rootkit while the Windows system is whirring away. Extracting malware is far easier when Windows is off.
Get a copy of Windows Defender Offline beta
As best I can tell ? Microsoft hasn?t published the details ? WDO will work on Windows XP SP3 systems (and possibly SP2); Vista RTM, SP1, and SP2; Windows 7 RTM and SP1; and Windows 8 Developer Preview. Also, your system must be bootable from a USB drive or a CD drive.
There are separate versions of WDO for 32-bit and 64-bit Windows, so you need to know the bittedness of the system to be scanned. (If you need help, see the Microsoft Help & How-to page, ?Is my PC running the 32-bit or 64-bit version of Windows??)
You can download WDO and create the bootable CD or USB drive on any handy computer, as long as it?s connected to the Internet. Here?s how:
1. Go to the Windows Defender Offline Beta site and, at the bottom of the page, click the link for either the 32-bit or 64-bit version. (Note, that the version needs to match the bittedness of the machine you?re fixing ? the bittedness of the machine you?re using to download WDO and create a bootable disc or drive doesn?t matter.)
2. Run the downloaded file to start the WDO installer ? you?ll see an initial splash screen with general WDO information. Click Next, and a new window appears that lets you choose where to install WDO, as shown in Figure 1. (Caution: Select the bootable USB drive option, and the installer wipes out everything currently on the USB drive.)

Figure 1. WDO must be installed on bootable media. The ISO-file option is used primarily to boot virtual machines.
3. Make your media selection and click Next. The installer downloads the latest version of the software and signature files (about 210MB for the 32-bit version or 230MB for the 64-bit version) and then creates the boot drive or the ISO file.
If you have problems creating a bootable drive, Microsoft?s WDO FAQ might have the answer.
Check your PC with Windows Defender Offline
It?s now time to boot your suspect system with the newly created WDO CD, DVD, or USB drive. If you need help with this step ? or your system won?t recognize the boot media (due, for example, to incorrect BIOS settings) ? the WDO FAQ page has some possible solutions (although the suggestion for disabling DEP is completely unnecessary).
If you have a multiboot system, you must choose which operating system to scan ? WDO will check only one at a time. With the OS selected, WDO next displays its command screen. (See Figure 2.)

Figure 2. Windows Defender Offline?s command screen looks a lot like Microsoft Security Essentials.
If it?s been a while since you created the WDO boot drive and the PC being scanned is connected to the Internet, you?ll most likely want to click the Update tab and download the latest definition files.
Before clicking the Scan now button, select from the Quick, Full, or Custom scan options. A full scan is very thorough ? it looks inside all the files on the system, including ancient backed-up e-mails ? and can take up to eight hours to complete. (In tests on a relatively fresh Windows 8 Developer Preview virtual machine, a full scan took only 20 minutes.) The Custom option lets you select specific drives and folders to scan. A Quick scan looks in the most commonly used locations on your PC.
If WDO finds potential threats, it displays warnings identical to those in Microsoft Security Essentials ? and, like MSE, it lets you remove, quarantine, or ignore each threat.
Microsoft?s ongoing problem of brand confusion
Microsoft seems to be playing around with ? and botching ? its brands again. You may remember the Windows Live ID branding stupidity: the same product was originally called Microsoft Wallet, then MS Passport, then .NET Passport, then MS Passport Network before finally being christened Windows Live ID. Similarly, MSN Messenger became MSN Messenger Service, which ran on the .NET Messenger Service (or was it Windows Messenger?); then it all suddenly morphed into Windows Live Messenger. The term .NET has gone through so many marketing wringers, it?s hard to keep track: is .NET a floor wax or a dessert topping? Microsoft has a habit of bewildering you with product name changes and confusing product pedigrees for no apparent reason; the term Windows Defender is about to join the club.
The branding history of WDO goes something like this. Back in 2004, Microsoft bought a company called GIANT AntiSpyware and turned that product into Microsoft AntiSpyware the next year. MS then rewrote it and renamed it Windows Defender in 2006 ? and made it a free download for Windows XP. Later, MS built Windows Defender into Vista and Windows 7.
In 2005, Microsoft also bought a company called Sybari and turned Sybari?s antivirus product into a corporate AV suite ? Microsoft Forefront. Many companies are still running Forefront.
Microsoft then created a free, consumer/small-business version of Forefront and called it Microsoft Security Essentials. If you download and install MSE on a PC that has Windows Defender (whether manually installed on XP or baked into Vista and Win7), it automatically disables the Windows Defender user interface and takes over Defender?s functions ? MSE effectively supersedes Windows Defender.
It now appears that Microsoft is recycling the Windows Defender name, but none of the original WD code. Windows President Steve Sinofsky, who?s in the thick of finishing Windows 8, stated in a Building Windows 8 blog, ?With Windows 8, we are extending the protections provided by Defender to address a broader range of potential threats.? He added that Win8 will have ?improvements to Windows Defender to provide you with real-time protection from all categories of malware ?.?
In short, there?s every indication that Windows Defender Offline is based on the Forefront/Microsoft Security Essentials code base and has absolutely nothing in common with the old Windows Defender ? regardless of what you may have read in the computer press.
Regardless of its history, Windows Defender Offline?s primary advantage is as a self-booting anti-malware system. Try it out!
