David Baxter PhD
Late Founder
WordPress blogs and more under global attack - check your passwords now!
by Paul Ducklin, Sophos.com
April 13, 2013
If you have a web service that supports remote users, you will know that malevolent login attempts are an everyday occurrence.
Even on my own home-hosted SSH server, listening unassumingly on an IP number on a DSL line, I've seen thousands of login attempts from dozens of different IP numbers in the course of a single day.
But hosting providers worldwide are reporting that they've been seeing systematic attempts, over the last 48 hours or so, to breach blogs and content management systems (CMSes) at well above average levels.
The primary target seems to be WordPress, with Joomla users also reportedly getting a bit of a hammering.
Word from the anti-DDoS world is that a botnet is responsible, with estimates of "up to 90,000," "more than tens of thousands," and "up to 100,000" infected computers (all those figures can be true at the same time, of course) orchestrating the felonious login attempts.
Since it would take too long to try every possible username and password on every known WordPress or Joomla server, this onslaught is using what is known as a dictionary attack.
That's where a crook settles on a list of the most likely usernames and passwords, and tries those in quick succession.
The idea is simple: automate the password guessing, speed up the attack, and don't spend too long on any individual site.
Look for the low-hanging fruit, and harvest it as quickly as you can; if you can't get in within a few hundred or thousand attempts, move on to the next potential victim.
It's doorknob rattling, but on an industrial and international scale.
Tireless cybercrime and underweb reporter Brian Krebs has published a list of sample WordPress usernames and passwords used in this attack, courtesy of security breach cleanup company Sucuri.
The top thirteen generically-chosen dictionary entries for username and password are as follows:
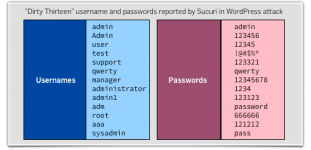
It's worth a look at the list (click on the image above), if only to reassure yourself that you haven't taken chances with any of your own passwords.
Notice also that the attackers are focusing on the username admin, used in 90% of the login attempts, because it's the default WordPress administrative username.
A username shouldn't be considered a secret (that's what the password is for), but you can avoid unwanted attention from low-hanging-fruit attacks by choosing something other than the default, as WordPress founder Matt Mullenweg himself advises.
Matt's suggestions are pithy and clearly put, so I'll repeat them here; they make up good advice for any web service product, whether you're blogging, file sharing, or running a CMS:
Almost 3 years ago we released a version of WordPress (3.0) that allowed you to pick a custom username on installation, which largely ended people using "admin" as their default username. Right now there’s a botnet going around all of the WordPresses it can find trying to login with the "admin" username and a bunch of common passwords, and it has turned into a news story (especially from companies that sell "solutions" to the problem).
Here’s what I would recommend: If you still use "admin" as a username on your blog, change it, use a strong password, if you’re on WP.com turn on two-factor authentication, and of course make sure you're up-to-date on the latest version of WordPress. Do this and you'll be ahead of 99% of sites out there and probably never have a problem. Most other advice isn't great — supposedly this botnet has over 90,000 IP addresses, so an IP limiting or login throttling plugin isn't going to be great (they could try from a different IP a second for 24 hours).
There you have it.
Not being the low-hanging fruit isn't a generic solution to this problem, as it's a bit like outrunning your buddy when you are chased by a hungry lion: it saves you, but leaves someone else to take the hit.
But that is no reason not to move your fruit to higher branches.
Remember that if someone breaks into your server, that's bad for you, but it is also bad for everyone else.
It gives the crooks a free ride for hosting malware, launching further attacks, publishing phishing pages, disseminating fake updates or bogus information, and much more.
All with your imprimatur, and, in the end, with your services blocklisted by anyone who's security conscious.
Remember, password-guessing attacks of this sort happen all the time.
The attack volume in this case has been sufficient to attract global attention, which is a good thing, but it's currently thought to be only about three times the usual level.
In other words, even when "normal service" is resumed, we'll all still be firmly in the sights of the cybercriminals, so take this as a spur to action!
by Paul Ducklin, Sophos.com
April 13, 2013
If you have a web service that supports remote users, you will know that malevolent login attempts are an everyday occurrence.
Even on my own home-hosted SSH server, listening unassumingly on an IP number on a DSL line, I've seen thousands of login attempts from dozens of different IP numbers in the course of a single day.
But hosting providers worldwide are reporting that they've been seeing systematic attempts, over the last 48 hours or so, to breach blogs and content management systems (CMSes) at well above average levels.
The primary target seems to be WordPress, with Joomla users also reportedly getting a bit of a hammering.
Word from the anti-DDoS world is that a botnet is responsible, with estimates of "up to 90,000," "more than tens of thousands," and "up to 100,000" infected computers (all those figures can be true at the same time, of course) orchestrating the felonious login attempts.
Since it would take too long to try every possible username and password on every known WordPress or Joomla server, this onslaught is using what is known as a dictionary attack.
That's where a crook settles on a list of the most likely usernames and passwords, and tries those in quick succession.
The idea is simple: automate the password guessing, speed up the attack, and don't spend too long on any individual site.
Look for the low-hanging fruit, and harvest it as quickly as you can; if you can't get in within a few hundred or thousand attempts, move on to the next potential victim.
It's doorknob rattling, but on an industrial and international scale.
Tireless cybercrime and underweb reporter Brian Krebs has published a list of sample WordPress usernames and passwords used in this attack, courtesy of security breach cleanup company Sucuri.
The top thirteen generically-chosen dictionary entries for username and password are as follows:

It's worth a look at the list (click on the image above), if only to reassure yourself that you haven't taken chances with any of your own passwords.
Notice also that the attackers are focusing on the username admin, used in 90% of the login attempts, because it's the default WordPress administrative username.
A username shouldn't be considered a secret (that's what the password is for), but you can avoid unwanted attention from low-hanging-fruit attacks by choosing something other than the default, as WordPress founder Matt Mullenweg himself advises.
Matt's suggestions are pithy and clearly put, so I'll repeat them here; they make up good advice for any web service product, whether you're blogging, file sharing, or running a CMS:
Almost 3 years ago we released a version of WordPress (3.0) that allowed you to pick a custom username on installation, which largely ended people using "admin" as their default username. Right now there’s a botnet going around all of the WordPresses it can find trying to login with the "admin" username and a bunch of common passwords, and it has turned into a news story (especially from companies that sell "solutions" to the problem).
Here’s what I would recommend: If you still use "admin" as a username on your blog, change it, use a strong password, if you’re on WP.com turn on two-factor authentication, and of course make sure you're up-to-date on the latest version of WordPress. Do this and you'll be ahead of 99% of sites out there and probably never have a problem. Most other advice isn't great — supposedly this botnet has over 90,000 IP addresses, so an IP limiting or login throttling plugin isn't going to be great (they could try from a different IP a second for 24 hours).
There you have it.
Not being the low-hanging fruit isn't a generic solution to this problem, as it's a bit like outrunning your buddy when you are chased by a hungry lion: it saves you, but leaves someone else to take the hit.
But that is no reason not to move your fruit to higher branches.
Remember that if someone breaks into your server, that's bad for you, but it is also bad for everyone else.
It gives the crooks a free ride for hosting malware, launching further attacks, publishing phishing pages, disseminating fake updates or bogus information, and much more.
All with your imprimatur, and, in the end, with your services blocklisted by anyone who's security conscious.
Remember, password-guessing attacks of this sort happen all the time.
The attack volume in this case has been sufficient to attract global attention, which is a good thing, but it's currently thought to be only about three times the usual level.
In other words, even when "normal service" is resumed, we'll all still be firmly in the sights of the cybercriminals, so take this as a spur to action!
