David Baxter PhD
Late Founder
More than 600,000 Macs infected with Flashback botnet
by Steven Musil, CNet
April 4, 2012
Russian antivirus company says half the computers infected with malware designed to steal personal information are in the U.S. -- with 274 located in Cupertino.
More than half a million Macs are infected with the Flashback Trojan, a malware package designed to steal personal information, according to a Russian antivirus company.
The company -- Dr. Web -- originally reported today that 550,000 Macintosh computers were infected by the growing Mac botnet. But later in the day, Dr. Web malware analyst Sorokin Ivan announced on Twitter that the number of Macs infected with Flashback had increased to 600,000, with 274 of those based in Cupertino, Calif.
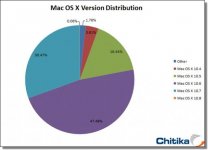
More than half of the Macs infected are in the United States (57 percent), while another 20 percent are in Canada, Dr. Web said.
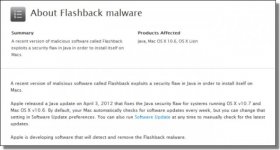
The malware was initially found in September 2011 masquerading as a fake Adobe Flash Player plug-in installer, but in the past few months it has evolved to exploiting Java vulnerabilities to target Mac systems. A new variant that surfaced over the weekend appears to be taking advantage of Java vulnerability for which Apple released a patch yesterday.
As CNET blogger Topher Kessler explains, simply visiting a malicious Web site containing Flashback on an OS X system with Java installed will result in one of two installation routes. The malware will request an administrator password, and if one is supplied, it will install its package of code into the Applications folder. If a password is not offered, the malware will install to the user accounts where it can run in a more global manner.
Once installed, the Flashback will inject code into Web browsers and other applications like Skype to harvest passwords and other information from those program's users.
Security company F-Secure has published instructions on how to determine whether a Mac is infected with Flashback.
by Steven Musil, CNet
April 4, 2012
Russian antivirus company says half the computers infected with malware designed to steal personal information are in the U.S. -- with 274 located in Cupertino.
More than half a million Macs are infected with the Flashback Trojan, a malware package designed to steal personal information, according to a Russian antivirus company.
The company -- Dr. Web -- originally reported today that 550,000 Macintosh computers were infected by the growing Mac botnet. But later in the day, Dr. Web malware analyst Sorokin Ivan announced on Twitter that the number of Macs infected with Flashback had increased to 600,000, with 274 of those based in Cupertino, Calif.
More than half of the Macs infected are in the United States (57 percent), while another 20 percent are in Canada, Dr. Web said.
The malware was initially found in September 2011 masquerading as a fake Adobe Flash Player plug-in installer, but in the past few months it has evolved to exploiting Java vulnerabilities to target Mac systems. A new variant that surfaced over the weekend appears to be taking advantage of Java vulnerability for which Apple released a patch yesterday.
As CNET blogger Topher Kessler explains, simply visiting a malicious Web site containing Flashback on an OS X system with Java installed will result in one of two installation routes. The malware will request an administrator password, and if one is supplied, it will install its package of code into the Applications folder. If a password is not offered, the malware will install to the user accounts where it can run in a more global manner.
Once installed, the Flashback will inject code into Web browsers and other applications like Skype to harvest passwords and other information from those program's users.
Security company F-Secure has published instructions on how to determine whether a Mac is infected with Flashback.